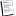
Well, by default and I just checked... Bypass Traverse checking is
applied to:
Administrators
Everyone
Backup Operators
Power Users
Users
This does not allow a user (who has no file/folder permissions) to
type in the full path and filename causing windows to attempt to open
a file with the associated program. However on a Network Appliance,
this appears to be the case. Let me restate that the file does not
get opened.. They get a generic access denied type of error. But the
fact that a user with no permissions can get this far into the file
system is alarming.. And it does break code for programmers who count
on the NTFS rights behaving as expected.
Thanks
Dead
"Lyle Meier" wrote in message ...
This is the behavior that one would get in NTFS if one applied the bypass
traverse checking
option in the user rights area. The behavior is listed as being needed if
one wants to run
the posix subsystem, so the NetApp behavior is not surprising given its
heritage.
"Deadgame" wrote in message
om...
Has anyone seen this? we are new to network appliance, our company
has just decided to start getting these units instead of other SAN/NAS
solutions that would have a windows kernel rather than unix. It
started when one of our developers was alerted to errors in one of
their applications. This application was written in VB and would use
the end user's NTFS permissions to traverse a directory structure.
Our developer would trap for error 50 which would just convieniently
keep the user from seeing directories they did not have access.
It appears the behavior of a CIFS share is a bit different from a real
windows NTFS share, if you know the full path of a file, you can
actually browse the directory structure and even attempt to open the
file, if you do not have rights, you will not be able to open the
file, but you can almost do it. If you type in the full path and file
name the windows client will attempt to open this file using the
associated file type. This produces an error 75 instead of 50. This
is in contrast to a real NTFS share where if you do not have rights to
the directory you cannot see past that directory, the client cannot
even see it by typing the full path and file name in the explorer
address bar. Now I am not a super hacker or anything I don't even
know how much more can be done, but it appears that Windows NTFS Share
is actually more secure than a Ontap CIFS Share.
If anybody knows of a tweak I could try please let me know. I have
opened a case with Network appliance and will be pursuing this with
them at the beginning of the week.


|